What to expect with your iOS/iPadOS that is managed by a MAM (App Protection Policy)
Overview
This knowledge base article describes what to expect when your iOS/iPadOS is managed by app protection policy settings.
Requirements
- Microsoft Intune tenant with MDM Authority set to Intune
- Minimum Apple iOS/iPadOS 15.0 and later
- Unmanaged iOS Microsoft Authenticator (broker app)
- Conditional Access Policy
- Microsoft Entra ID P1 (part of E3/E5 bundle)
Configuration
Devicie offers the following App Protection policies:
| Policy Name | Description |
| Devicie - iOS/iPadOS Enterprise Basic Data Protection | This app protection policy ensures that apps with work or school account data are protected with a PIN, encrypted, and enables selective wipe operations. |
| Devicie - iOS/iPadOS Enterprise Enhanced Data Protection | This app protection policy introduces data leakage prevention mechanisms and minimum OS requirements. This is the configuration that is applicable to most mobile users accessing work or school data. |
| Devicie - iOS/iPadOS Enterprise High Data Protection | This app protection policy is for devices used by specific users or groups who are uniquely high risk (for example, users who handle highly sensitive data where unauthorized disclosure causes considerable material loss to the organization). |
Apps
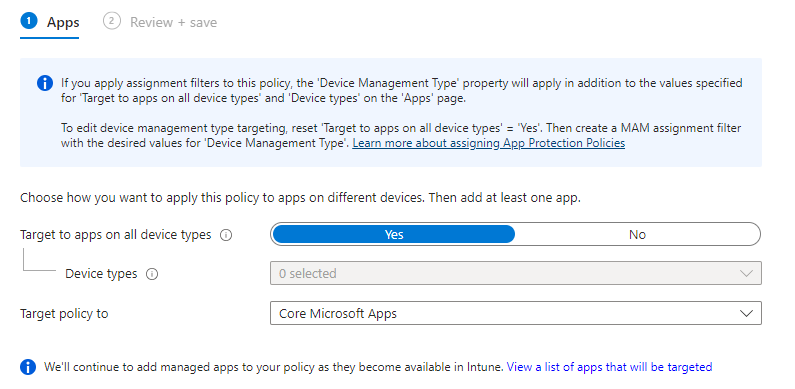
For each Devicie App Protection Policy, the Apps customised settings show the following:
- Target to apps on all device types: Yes
- Device types: 0 selected
- Target policy to: Core Microsoft Apps
Conditional Access policy
This conditional access policy requires the mobile devices is registered in Entra ID via a broker app. The broker app uses the Microsoft Authenticator for iOS, if the broker app is not available on a device, the user will be asked to download it during the sign-in process into one of the protected apps).
Create conditional access policy under Remote work: Require approved client apps and app protection
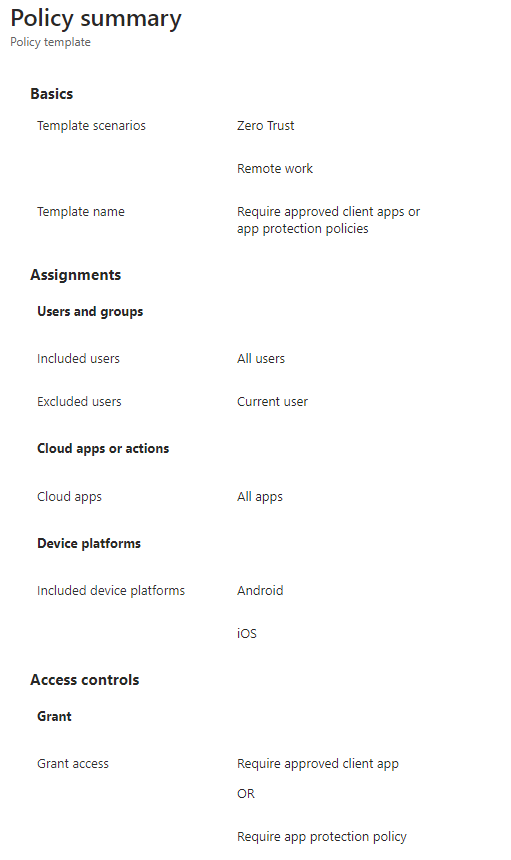
Target resources: All cloud apps
Device platforms: Android and iOS
Grant access controls: Require approved client app or Require app protection policy
For multiple controls: Require one of the selected controls
User Experience - Microsoft Outlook
Users downloads Microsoft Outlook on an unmanaged iOS/iPadOS device then signs in with corporate credentials.
When setting up Outlook, the user will be get redirected to the App store to install Microsoft Authenticator (broker app) when trying to authenticate for the first time.
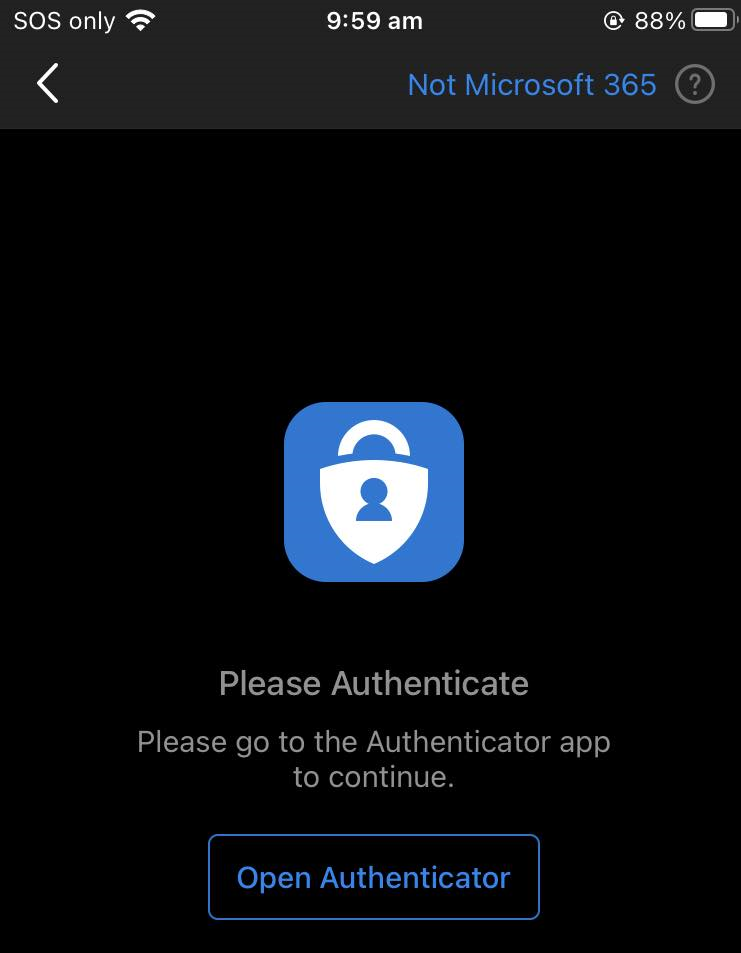
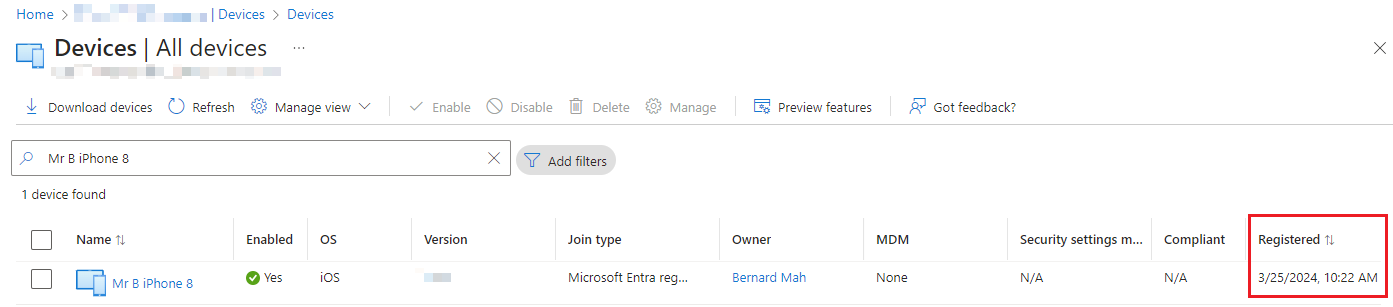
The broker app starts the Entra registration process which creates a device record in Entra ID (not Intune MDM), that record is necessary for the Conditional Access policies.
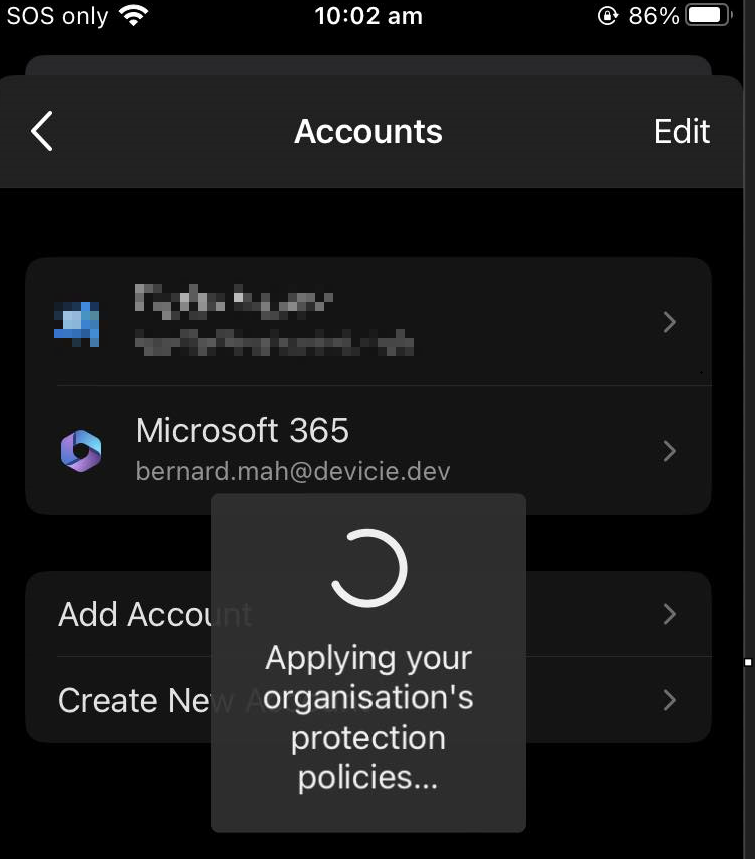
It will then apply the "App protection policy" as defined from Microsoft Intune onto the app.
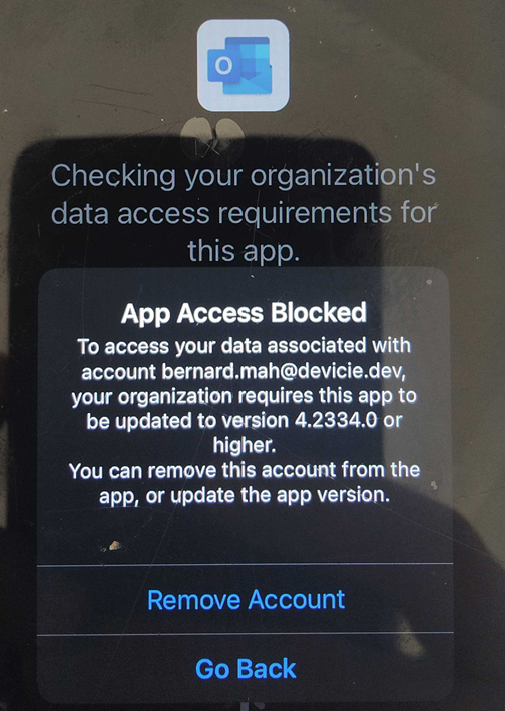
If you have an out-of-date Outlook iOS app version, this is what you get prompted to either "Remove Account" or update the application.
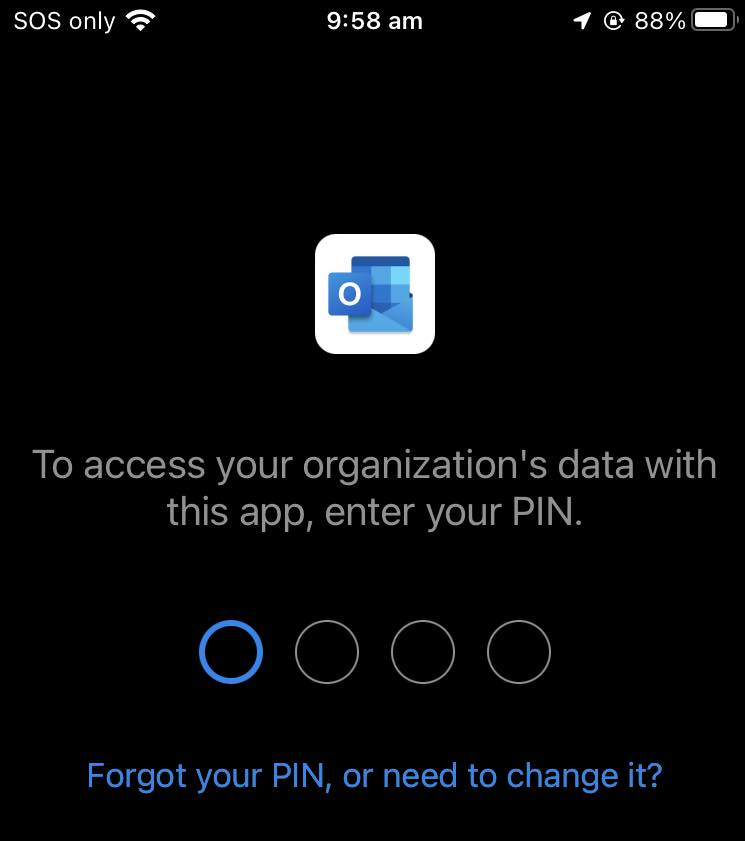
As per policy requirements, a user will need to setup a PIN for the app access on the iOS that is shared between other apps. As an example, if the user has not accessed the Outlook App on the mobile phone for more than 30 minutes, the user will be prompted to enter the 4 digit PIN.
User Experience - Microsoft Teams
The same process applies with Microsoft Teams.
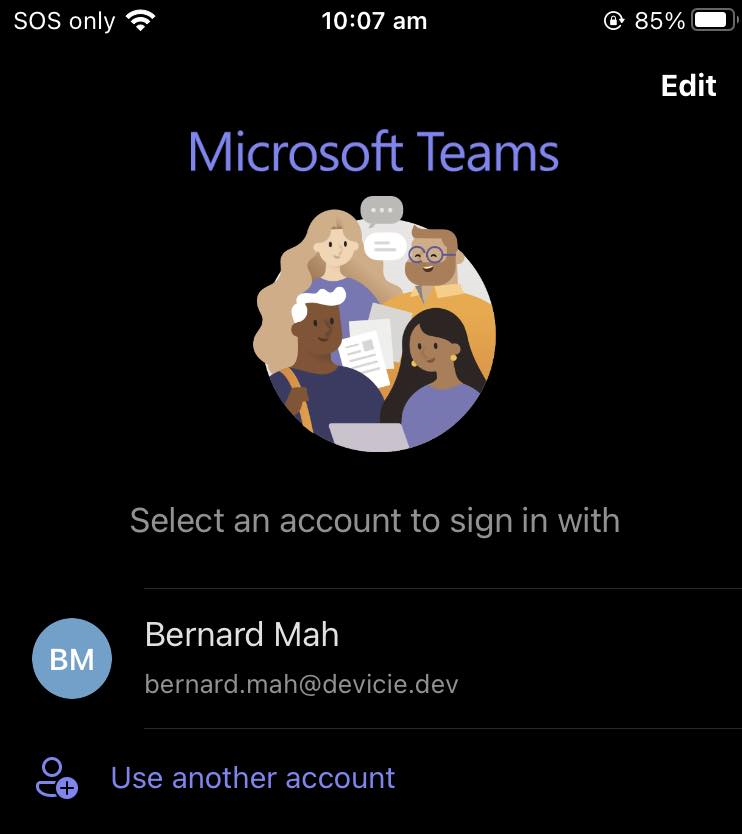
After logging into Microsoft Teams, it will use the iOS Microsoft Authenticator to authenticate which will apply the "App Protection policy" that is applied.
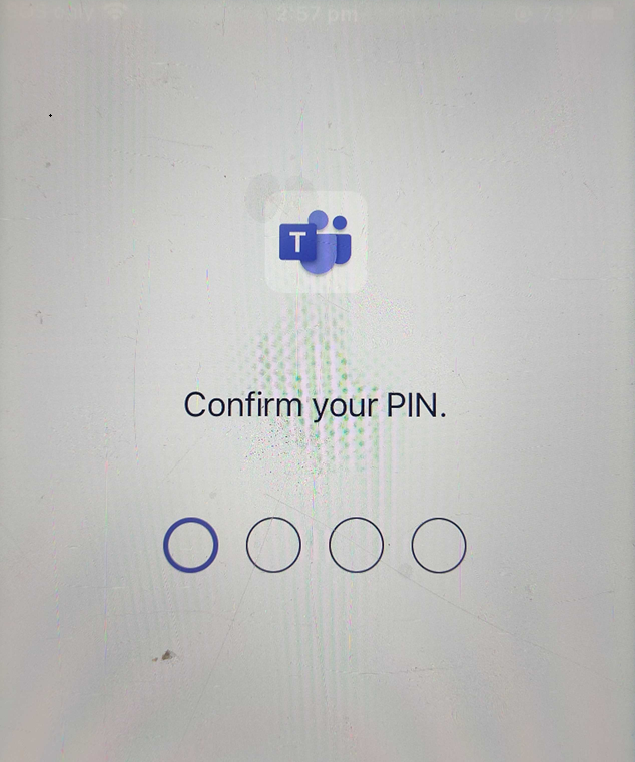
The user will be prompted to setup a 4 digit PIN.
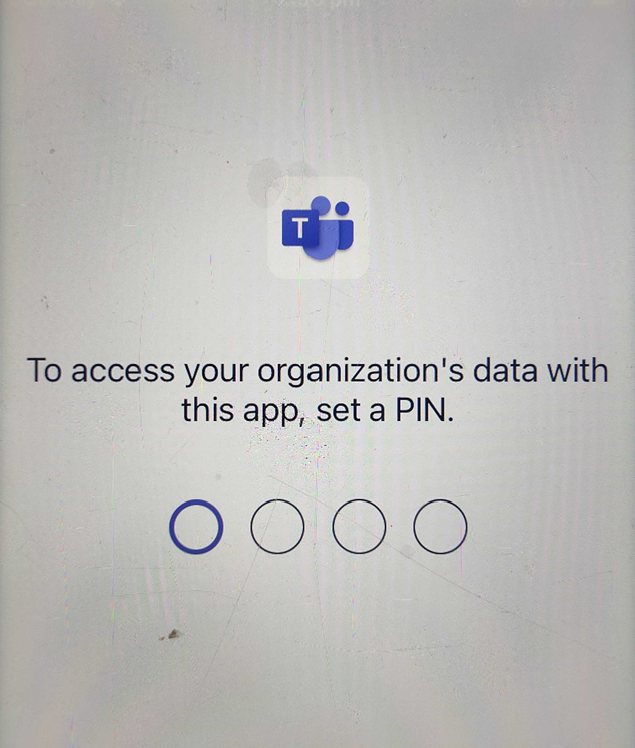
You will then be prompted to reconfirm your PIN. This will then load into Microsoft teams.
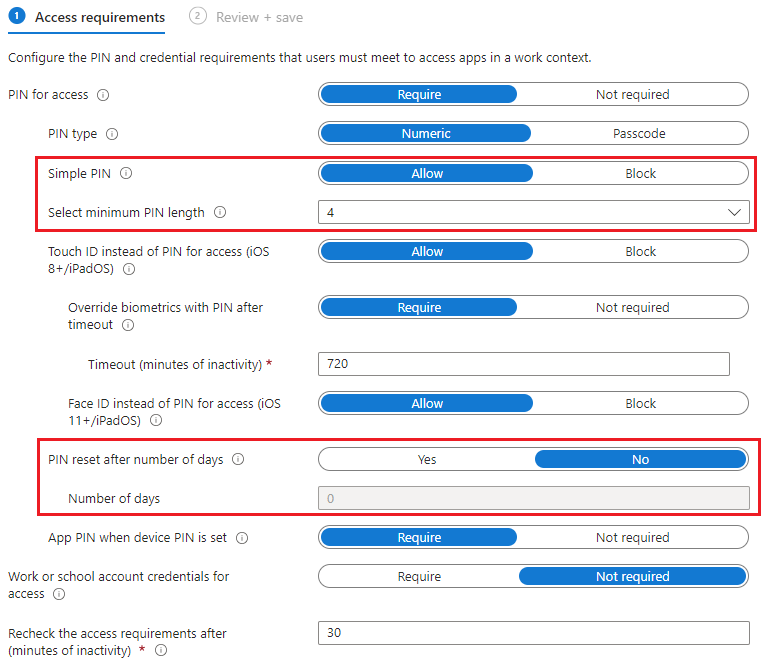
App Protection Policies - Differences
For Devicie - iOS/iPadOS Enterprise Basic Data Protection and Devicie - iOS/iPadOS Enterprise Enhanced Data Protection
- Simple PIN is set to Allow
- Select minimum PIN length is set to 4
- PIN reset after number of days is set to No
- Number of days is 0 (Not configured)
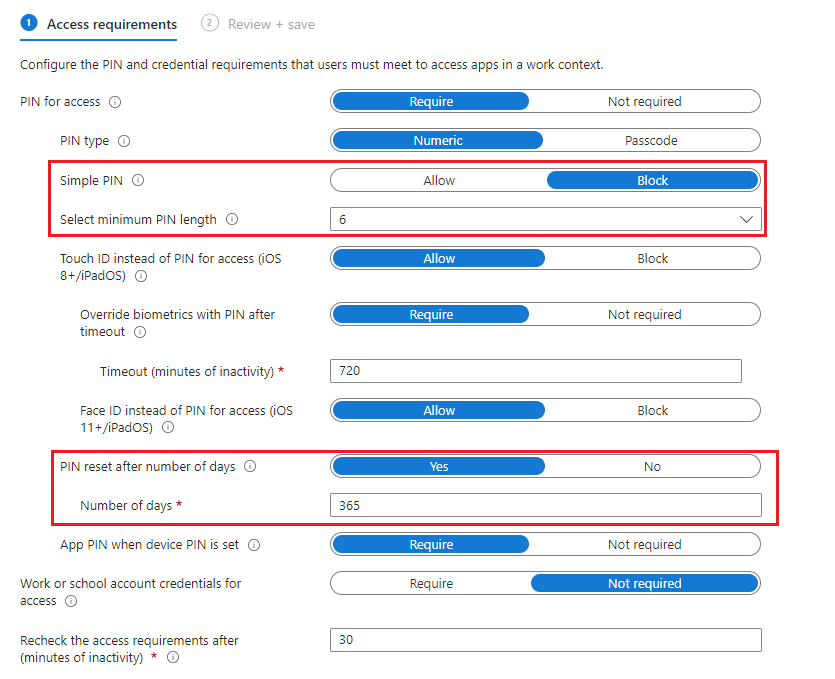
For Devicie - iOS/iPadOS Enterprise High Data Protection
- Simple PIN is set to Block
- Select minimum PIN length is set to 6
- PIN reset after number of days is set to Yes
- Number of days is 365