What does App Protection (MAM): Devicie - Android Enterprise Basic Data Protection offer?
Overview
This knowledge base article explains what does App Protection (MAM): Devicie - Android Enterprise Basic Data Protection offer and breakdown on the recommended values.
This will be broken down into three categories:
- Android Data Protection
- Android Data Protection: Data Transfer
- Android Data Protection: Encryption
- Android Data Protection: Functionality
- Android Access requirements
- Android Conditional launch
- Android Conditional Launch App conditions
- Android Conditional Launch Device condition
Android Data Protection: Data Transfer
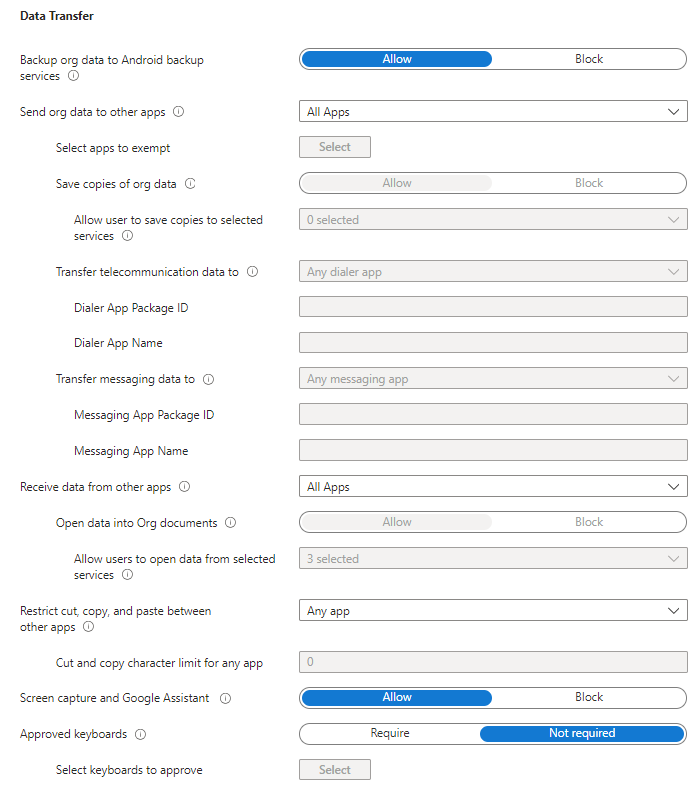
| Setting | Description | Default value |
| Backup org data to Android backup services |
|
Allow |
| Send Org data to other apps |
|
All Apps |
| Select apps to exempt | This option is available when you select Policy managed apps for the previous option. | N/A |
| Save copies of org data |
|
Allow |
| Allow user to save copies to selected services |
Users can save to the selected services:
All other services not listed will be blocked. |
0 selected |
| Transfer telecommunication data to |
When a user selects a hyperlinked phone number in an app, a dialer app will open with the phone number prepopulated and ready to call. For this setting, choose how to handle this type of content transfer when it is initiated from a policy-managed app:
|
Any dialer app |
| Dialer App Package ID | When a specific dialer app has been selected, you must provide the app package ID. | Blank |
| Dialer App Name | When a specific dialer app has been selected, you must provide the name of the dialer app. | Blank |
| Transfer messaging data to |
When a user selects a hyperlinked messaging link in an app, a messaging app will open with the phone number prepopulated and ready to send. Select the following type of content transfer from a policy-managed app:
|
Any messaging app |
| Messaging App Package ID | When a specific messaging app has been selected, you must provide the app package ID. | Blank |
| Messaging App Name | When a specific messaging app has been selected, you must provide the name of the messaging app. | Blank |
| Receive data from other apps | Specify what apps can transfer data to this app:
|
All apps |
| Open data into Org documents |
Select "Block" to disable the use of the Open option or other options to share data between accounts in this app. Select "Allow" if you want to allow the use of Open. When set to Block you can configure the Allow user to open data from selected services to specify which services are allowed for Org data locations.
|
Allow |
| Allow users to open data from selected services |
Select the application storage services that users can open data from. All other services are blocked. Selecting no services will prevent users from opening data from external locations.
|
All selected |
| Restrict cut, copy and paste between other apps |
Select the following:
|
Any app |
| Cut and copy character limit for any app |
Enter the number of characters that to cut or copy from Org data and accounts.
Note: Requires Intune Company Portal version 5.0.4364.0 or later |
0 |
| Screen capture and Google Assistant |
Select "Block" to block screen capture and block Google Assistant accessing org data on the device when using this app. Selecting Block will also blur the App-switcher preview image when using this app with a work or school account.
|
Allow |
| Approved keyboards |
Select Require and then specify a list of approved keyboards for this policy. Note: This setting requires the app to have the Intune SDK for Android version 6.2.0 or later. |
Not required |
| Select keyboards to approve |
This option is available when you select Require for the previous option. Choose Select to manage the list of keyboards and input methods that can be used with apps protected by this policy. You can add additional keyboards to the list, and remove any of the default options. You must have at least one approved keyboard to save the setting. Over time, Microsoft may add additional keyboards to the list for new App Protection Policies, which will require administrators to review and update existing policies as needed.
|
Not selected |
Android Data Protection: Encryption

| Setting | Description | Default Value |
| Encrypt Org data |
Select "Require", to enable encryption of work or school data in this app. |
Require |
| Encrypt org data on enrolled devices |
|
Require |
Android Data Protection: Functionality
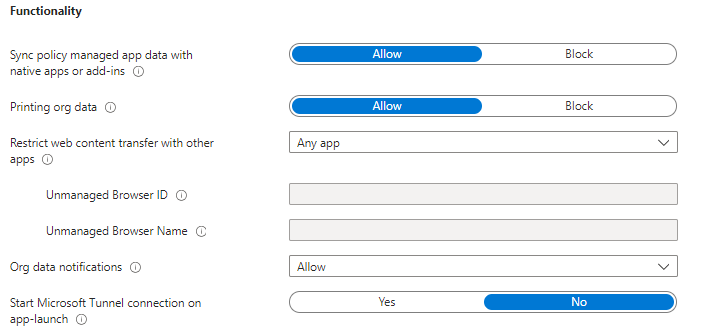
| Setting | Description | Default value |
| Sync policy managed app data with native apps or add-ins |
Select "Block" to prevent policy managed apps from saving data to the device's native apps (Contacts, Calendar and widgets) and to prevent the use of add-ins within the policy managed apps. If you choose Allow, the policy managed app can save data to the native apps or use add-ins, if those features are supported and enabled within the policy managed app. Note: When you perform a selective wipe to remove work, or school data from the app, data synced directly from the policy managed app to the native app is removed. Any data synced from the native app to another external source won't be wiped. |
Allow |
| Printing Org data |
|
Allow |
| Restrict web content transfer with other apps |
Select how web content (http/https links) is opened from policy-managed applications.
Note: Requires Intune Company Portal version 5.0.4415.0 or later. For Policy-managed browsers: On Android, your end users can choose from other policy-managed apps that support http/https links if neither Intune Managed Browser nor Microsoft Edge is installed.
For Policy-managed Microsoft Edge: The Microsoft Edge browser for mobile devices (iOS/iPadOS and Android) supports Intune app protection policies. Users who sign in with their corporate Microsoft Entra accounts in the Microsoft Edge browser application will be protected by Intune. The Microsoft Edge browser integrates the APP SDK and supports all of its data protection policies, with the exception of preventing:
|
Any app |
| Unmanaged Browser ID |
Enter the application ID for a single browser. Web content (http/https links) from policy managed applications will open in the specified browser. The web content will be unmanaged in the target browser. |
Blank |
| Unmanaged Browser Name |
Enter the application name for browser associated with the Unmanaged Browser ID. This name will be displayed to users if the specified browser is not installed. |
Blank |
| Org data notifications |
Specify how Org data is shared via OS notifications for Org accounts. This policy setting will impact the local device and any connected devices such as wearables and smart speakers. The following additional controls to customise behaviour:
Note: This setting requires the following app support:
|
Allow |
| Start Microsoft Tunnel connection on app-launch |
Allow connection to VPN when app is launch |
No |
Android Access Requirements
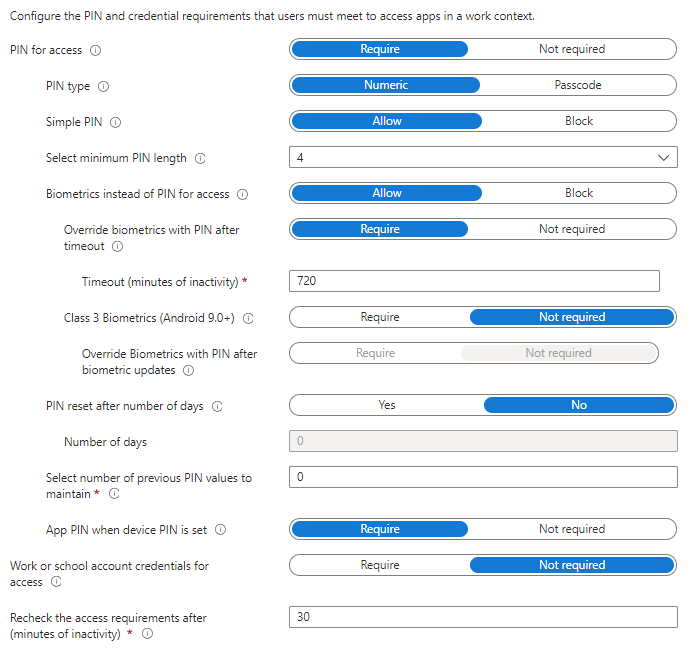
| Setting | Description | Default value |
| PIN for access |
Select "Require" this will require a PIN to use this app. The user is prompted to set up this PIN the first time they run the app in a work or school context. The PIN is applied when working either online or offline. You can configure the PIN strength using the settings available under the PIN for access section. |
Require |
| PIN type | Set a requirement for either numeric or passcode type PINs before accessing an app that has app protection policies applied. Numeric requirements involve only numbers, while a passcode can be defined with at least 1 alphabetical letter or at least 1 special character. | Numeric |
| Simple PIN |
|
Allow |
| Select minimum PIN length | This setting specifies the minimum number of digits in a PIN sequence. | 4 |
| Biometrics instead of PIN for access | Select "Allow" to allow the user to use biometrics to authenticate users on Android devices. If allowed, biometrics is used to access the app on Android 10 or higher devices. |
Allow |
| Override biometric with PIN after timeout | Select "Require" and then configure an inactivity timeout. | Require |
| Timeout (minutes of inactivity) | Select in minutes after which either a passcode or numeric (as configured) PIN will override the use of a fingerprint or face as method of access. This timeout value should be greater than the value specified under 'Recheck the access requirements after (minutes of inactivity)'. | 720 |
| Class 3 biometrics (Android 9.0+) | Select "Allow" to allow the user to use facial recognition technology to authenticate users on iOS/iPadOS devices. If allowed, Face ID must be used to access the app on a Face ID capable device. | Not required |
| Override biometrics with PIN after biometric updates |
Select "Require" to override the use of biometrics with PIN when a change in biometrics is detected. |
|
| PIN reset after number of days |
Select "Yes" to require users to change their app PIN after a set period of time, in days. If "Yes" is selected, then configure the number of days before the PIN reset is required. |
No |
| Number of days | Configure the number of days before the PIN reset is required. | 30 |
| Select number of previous PIN values to maintain |
This setting specifies the number of previous PINs that Intune will maintain. Any new PINs must be different from those that Intune is maintaining. |
0 |
| App PIN when device PIN is set |
Select "Not required" to disable the app PIN when a device lock is detected on an enrolled device with Company Portal configured. |
Require |
| Work or school account credentials for access | Select "Require", this will require the user to sign in with their work or school account instead of entering a PIN for app access. If you set this to Require, and PIN or biometric prompts are turned on, both corporate credentials and either the PIN or biometric prompts are shown. |
Not required |
| Recheck the access requirements after (minutes of inactivity) | Configure the number of minutes of inactivity that must pass before the app requires the user to again specify the access requirements. | 30 |
Android Conditional launch: App conditions
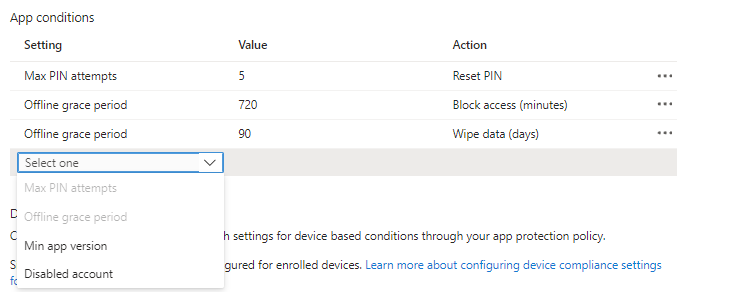
| Setting | Description |
| Max PIN attempts |
This setting specifies the number of tries the user has to successfully enter their PIN before the configured action is taken. The following actions include:
|
| Offline grace period |
This setting specifies the time (in minutes) before the access requirements for the app are rechecked. The following actions include:
|
| Min app version |
This setting specifies a value for the minimum application version value. The following actions include:
|
| Disabled version |
There is no value to set for this setting. Block access: When we have confirmed the user has been disabled in Microsoft Entra ID, the app blocks access to work or school data. |
Android Conditional launch: Device conditions
| Setting | Description |
| Jailbroken/rooted devices |
This setting specifies whether to block access to the device or wipe the device data for jailbroken/rooted devices.
|
| Min OS version |
This setting specifies the minimum Android operating system to use this app. OS versions below the minimum OS version will trigger the actions. Select the following actions:
|
| Max OS version |
This setting specifies the maximum Android operating system to use this app. OS versions below the minimum OS version will trigger the actions. Select the following actions:
|
| Min patch version |
This requires devices have a minimum Android security patch released by Google. Select the following actions:
|
| Device manufacturer(s) |
This specifies a semicolon separated list of manufacturers.
|
| Play integrity verdict |
This setting in particular configures Google's Play Integrity check on end user devices to validate the integrity of those devices. Select the following integrity:
The following actions include:
|
| Require threat scan on apps |
This setting in particular ensures that Google's Verify Apps scan is turned on for end user devices. If configured, the end user will be blocked from access until they turn on Google's app scanning on their Android device. The following actions include:
|
| Play Integrity verdict evaluation type |
This setting checks the hardware backed attestation, which enhances the existing SafetyNet attestation service check. You can set the value to Hardware-backed key after setting SafetyNet device attestation. |
| Require device lock |
This setting determines whether the Android device has a device PIN that meets the minimum password requirement. The App protection policy can take action if the device lock doesn’t meet the minimum password requirement. The following values include:
Note: The Complexity value is targeted to Android 12+. For devices operating on Android 11 and earlier setting a complexity value of low, medium or high will default to the expected behaviour for Low Complexity. The following actions include:
|
| Min Company Portal version |
This setting specifies minimum defined version of the Company Portal is enforced on an end user device. This conditional launch setting allows you to set values to Block access, Wipe data and Warn. |
| Max Company Portal version age (days) |
This settings sets a maximum number of days as the age of the Company portal version for Android devices. The value must be between 0 and 365 days. When the setting for the devices is not met, the action for this setting is triggered which includes:
Note: The age of the Company Portal build is determined by Google Play on the end user device. |
| Samsung Knox device attestation |
This setting specifies the Samsung Know device attestation check is required. View the list of supported Samsung devices. The following actions include:
|
| Max allowed device threat level |
This setting specifies a maximum threat level acceptable to use this app. Threats are determined by your chosen Mobile Threat Defense (MTD) vendor app on the end user device. Select the following options: Secured, Low, Medium, or High. Secured requires no threats on the device and is the most restrictive configurable value, while High essentially requires an active Intune-to-MTD connection. Actions include:
|
| Primary MTD service |
If you have configured multiple Intune-MTD connectors, specify the primary MTD vendor app that should be used on the end user device.
|