The common MAM (App Protection) questions, answers and policies
Overview
This knowledge base article provides information around the questions, answers and scenarios with App Protection policies for iOS and Android - Managed and Unmanaged devices.
This knowledge base article will be broken down into the following:
- App Protection Requirements
- App Protection target with Apps
- App Protection Delivery
- App Protection policies that conflict or occur
- App Protection actions based on user status
App Protection Requirements
The following Android and iOS/iPadOS requirements are:
- Minimum Android Operating System Version 9.0 or later
- Minimum iOS/iPadOS Operating System Version 15.0 or later
- Microsoft Authenticator (broker app) for iOS
- Microsoft Company Portal (broker app) for Android
App Protection target which Apps
When creating a new App Protection policy, the setting 'Target policy to' can be justified by selecting:
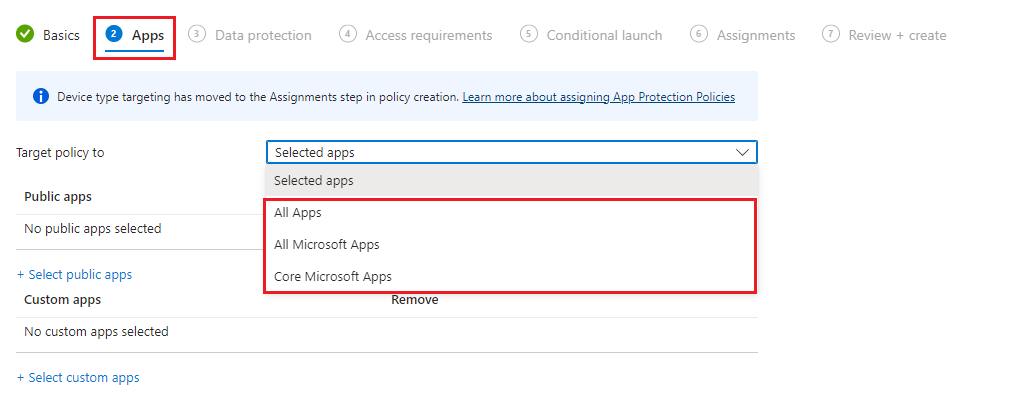
- All Apps: This will include all Core Microsoft Apps including other supported Intune apps.
- All Microsoft Apps: This will include all Microsoft Apps, Core Microsoft Apps and other supported Intune apps.
- Core Microsoft Apps include the following:
- Microsoft Edge
- Microsoft Excel
- Microsoft Office
- Microsoft OneDrive
- Microsoft OneNote
- Microsoft Outlook
- Microsoft PowerPoint
- Microsoft SharePoint
- Microsoft Teams
- To Do
- Microsoft Word
App Protection Delivery
App Protection Delivery times are dependent on license state and Intune service registration for users.
| User State | App Protection behaviour | Retry Interval | Why does this happen |
| Tenant not onboarded | Wait for next retry interval. App Protection isn't active for the user. | 24 hours | Occurs when you have not setup your tenant for Intune. |
| User not licensed | Wait for next retry interval. App Protection isn't active for the user. | 12 hours. However, on Android devices this interval requires Intune APP SDK version 5.6.0 or later. Otherwise for Android devices, the interval is 24 hours. | Occurs when you haven't licensed the user for Intune. |
| User not assigned App Protection Policies | Wait for next retry interval. App Protection isn't active for the user. | 12 hours | Occurs when you haven't assigned App Protection settings to the user. |
| User Assigned App Protection Policies but app isn't defined in the App Protection Policies | Wait for next retry interval. App Protection isn't active for the user. | 12 hours | Occurs when you haven't added the apps to App Protection policies. |
| User Successfully Registered for Intune MAM | App Protection is applied per policy settings. Updates occur based on retry interval | 30 minutes | Occurs when the user has successfully registered with the Intune service for APP configuration. |
Note: Retry intervals may require active app use to occur, meaning the app is launched and in use. If the retry interval is 24 hours and the user waits 48 hours to launch the app, the Intune APP SDK will retry at 48 hours.
App Protection policies that conflict or occur
Conflicting values are the most restrictive settings available in an app protection policy. The list of App Protection policies that do conflict are:- PIN Attempts before reset where numeric entry fields that are set the same as the values.
- When two profiles are similar, example would be 'Restrict cut, copy, and paste between other apps' where policy one will have setting: 'Any app' while policy two will have Policy managed apps'.
- When policy one is deployed, the first policy will take precedence and stays applied, when policy two is deployed, this will show a conflict.
- If both policies one and two are applied at the same time, there will be no preceding policy then both are in conflict.
- Web browsers for iOS and Android, for iOS the default browser is Safari (built-in) and default browser for Android is Google Chrome. This applies to setting 'Restrict web content transfer with other apps'. Ensure an iOS Store App, VPP (iOS) app, Android store app or Managed Google Play Store App (Android) like Microsoft Edge is deployed to corporate owned and personal devices.
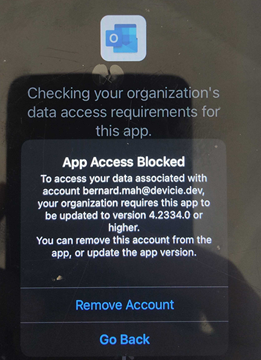
- Out of date store apps will prevent the user from setting up Outlook during the MAM process. The user will be prompted to remove account. Solution: Update the app to the latest version.
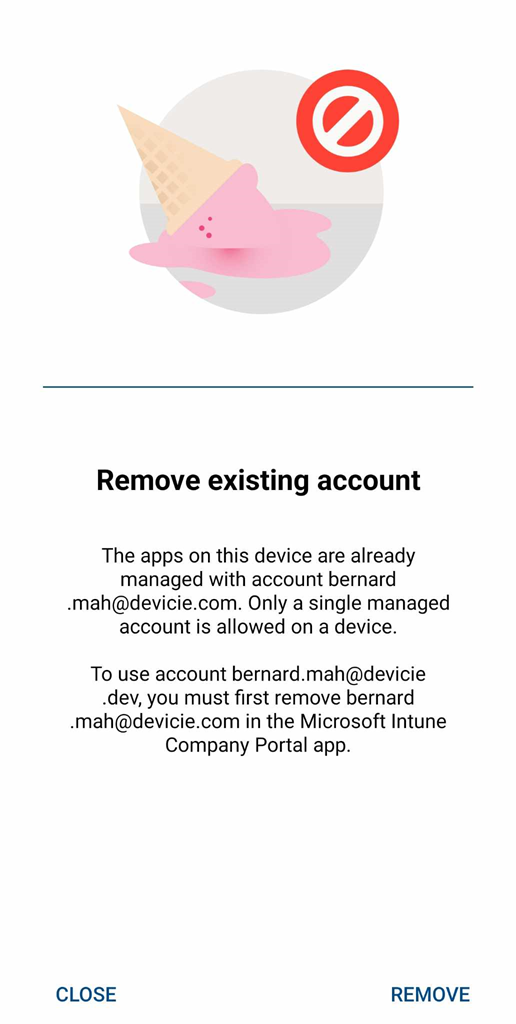
- If you have an existing MAM policy tied to a primary user account, and you wish to login with another secondary user account. When trying to add the secondary account details, you will get prompted to Remove or Close. Solution: Select Remove to proceed.
This will also prompt to confirm removal of the account associated in Android.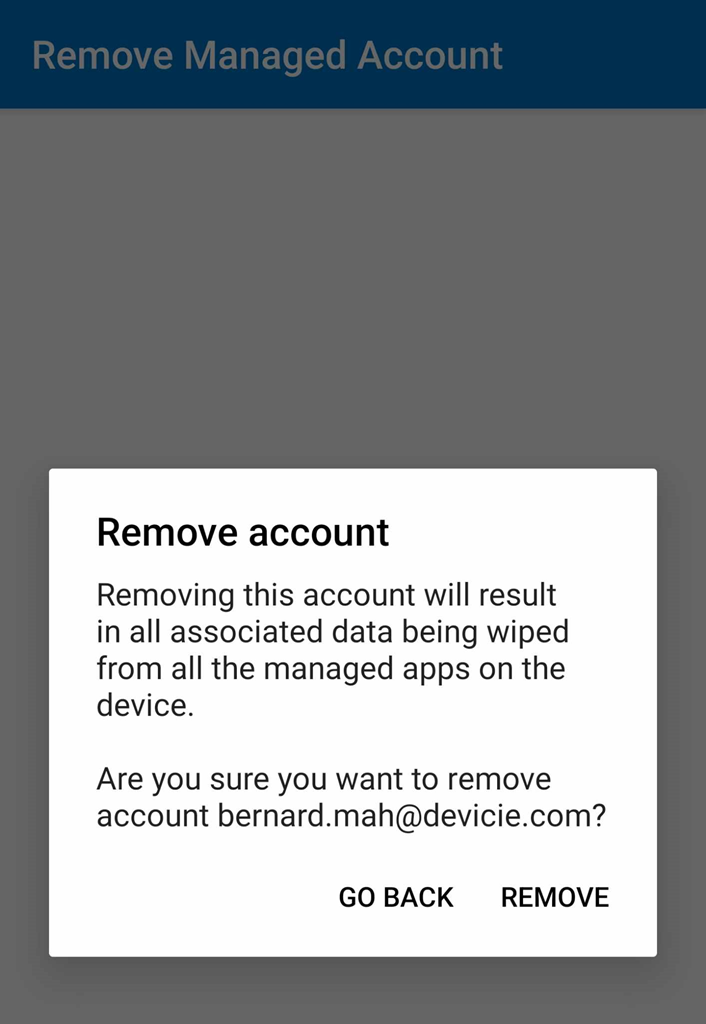
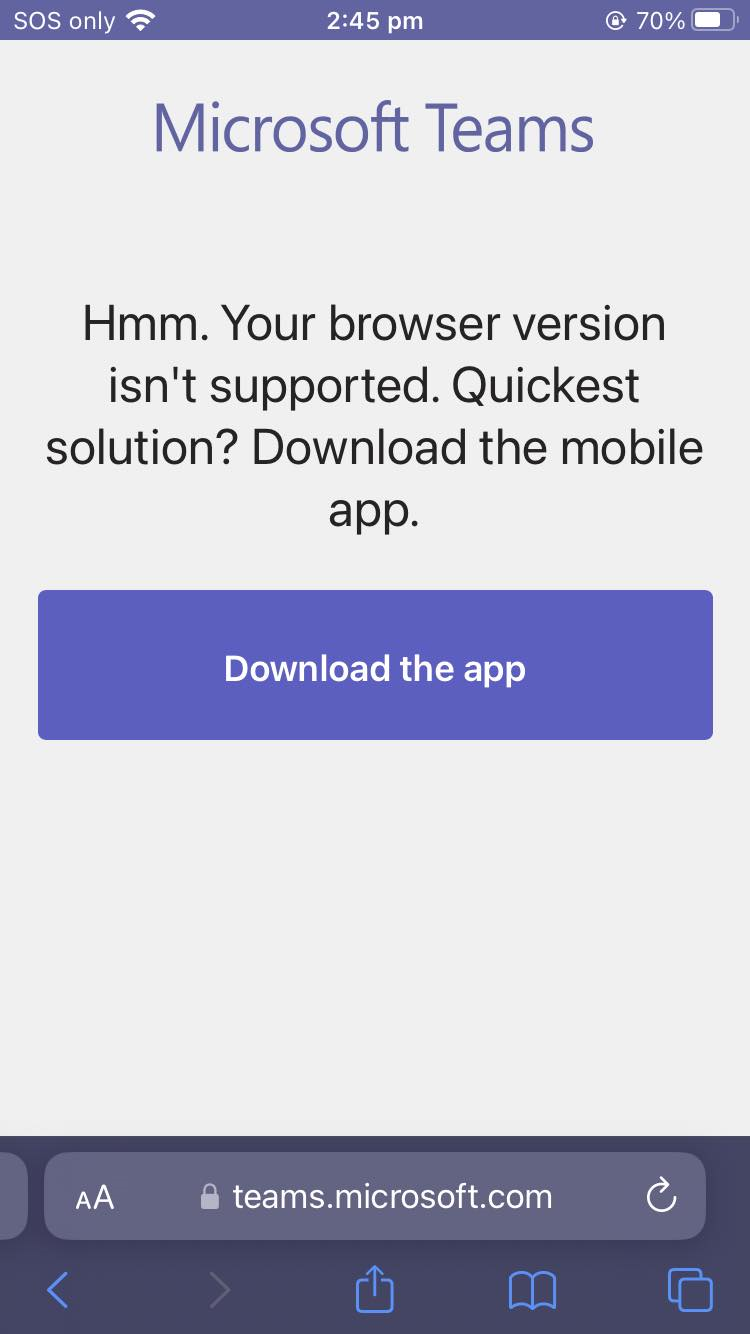
- When trying to access teams.microsoft.com on Safari, you will get prompted with the following. Solution: Download and install Microsoft Teams or use a managed browser like Microsoft Edge.
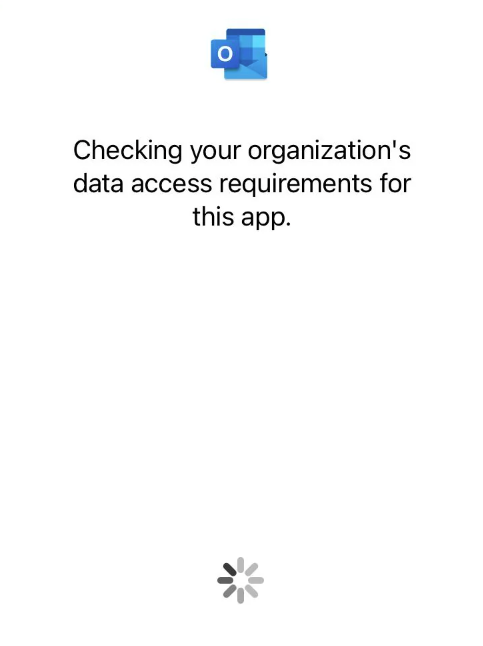
- After setting up your MAM policy on your mobile, this might be spinning for a long period of time. Suggestion: Uninstall Outlook App then re-install Outlook app then login with corporate credentials.
- After completing the iOS MAM setup policy, you will get this prompt.
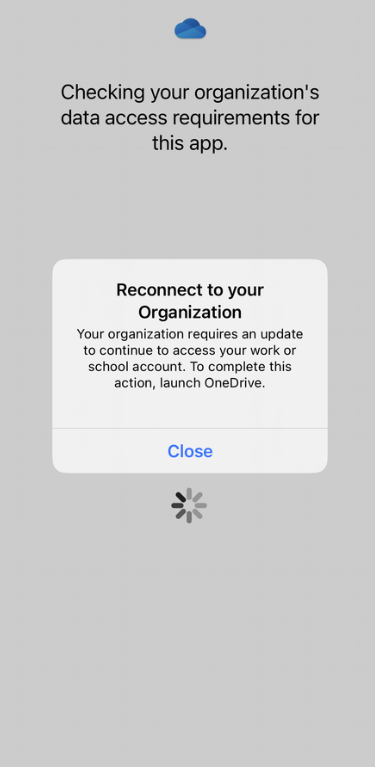
OR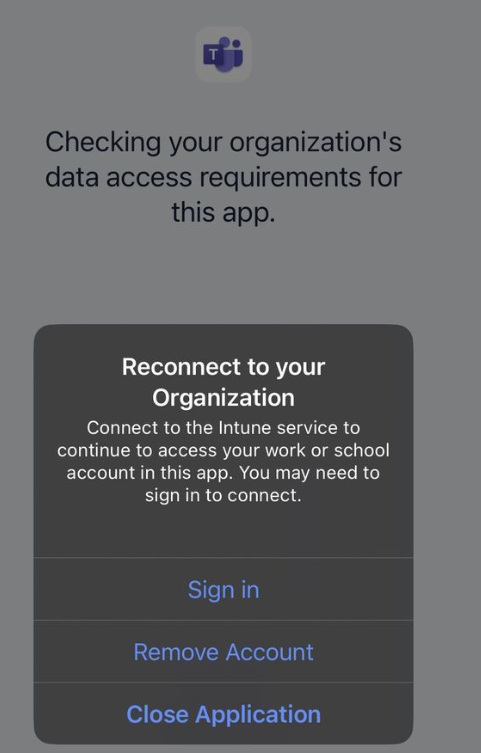
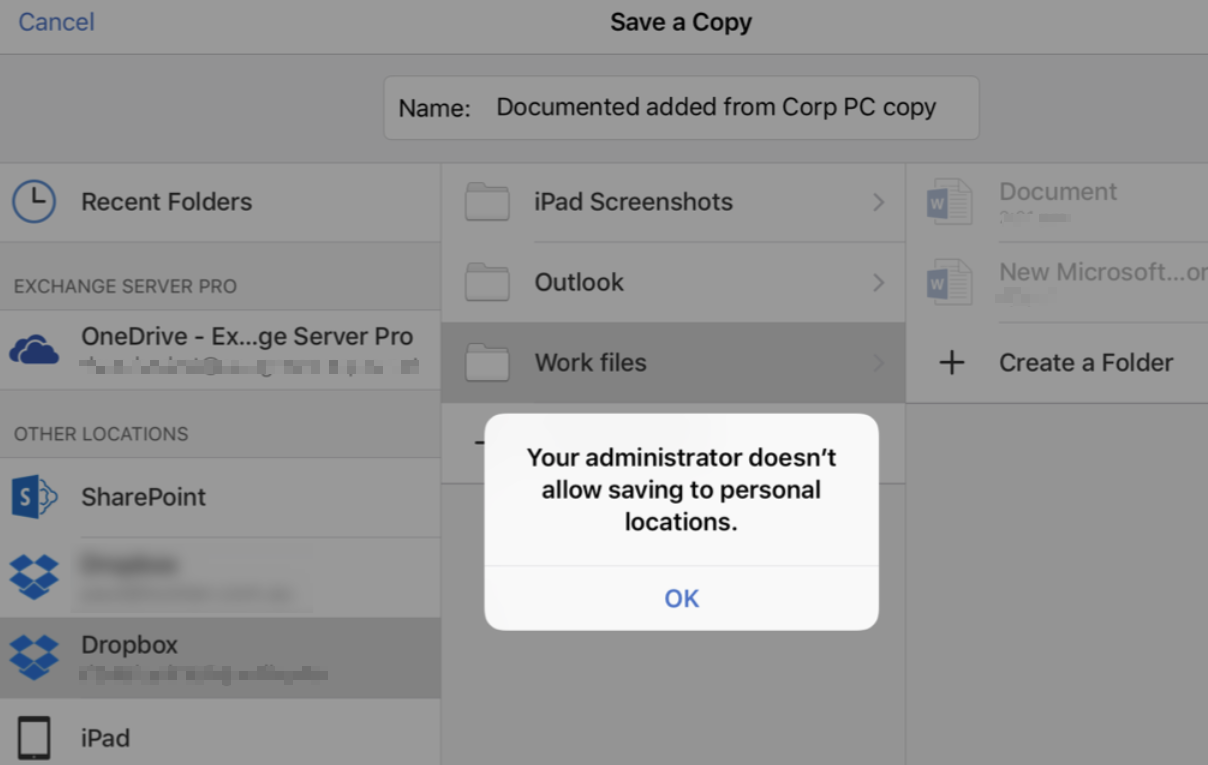
Workaround: You can navigate to Settings > OneDrive > Reset Word> Delete Login Credentials. - When a user is trying to save corporate data to unmanaged app like Dropbox, it will display the following. Solution: Users can only save to managed apps like OneDrive for Business.
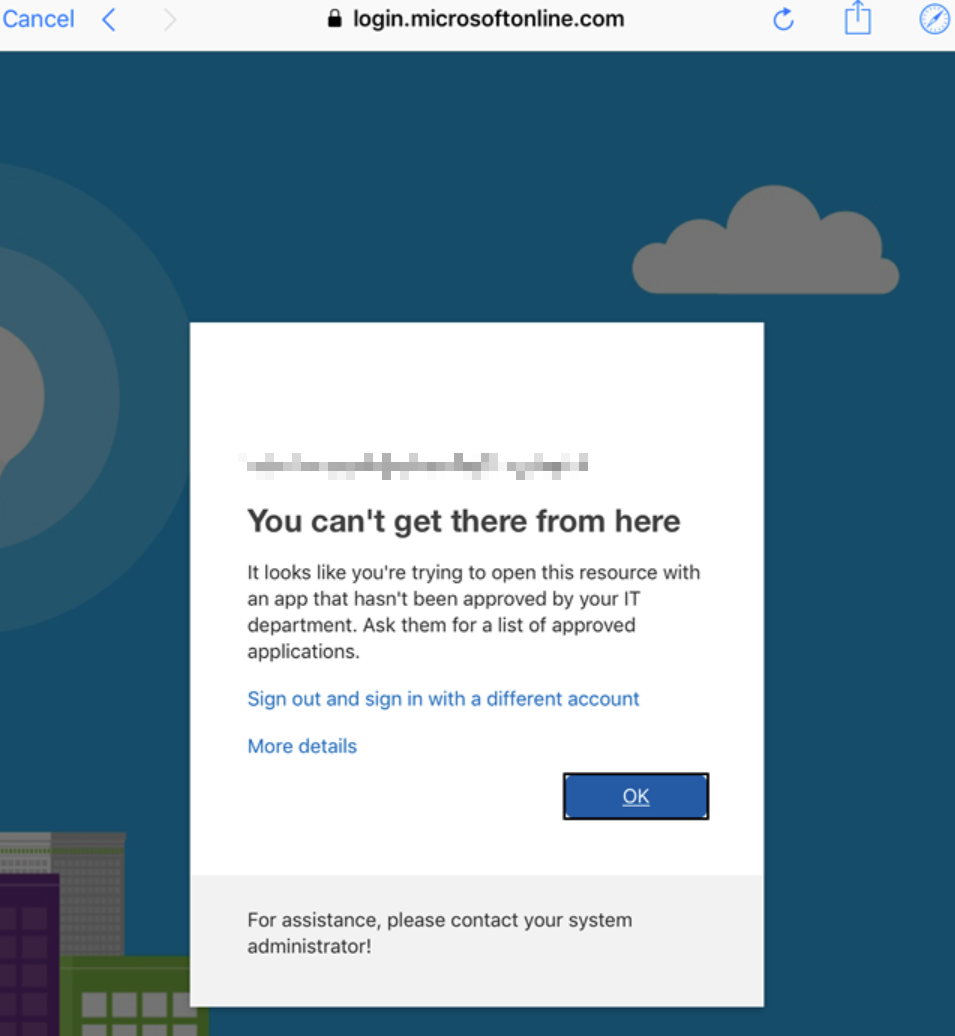
- When users try to access an app using iOS Safari, they will be prompted with the following message. Solution: User Microsoft Edge to access an Entra app.
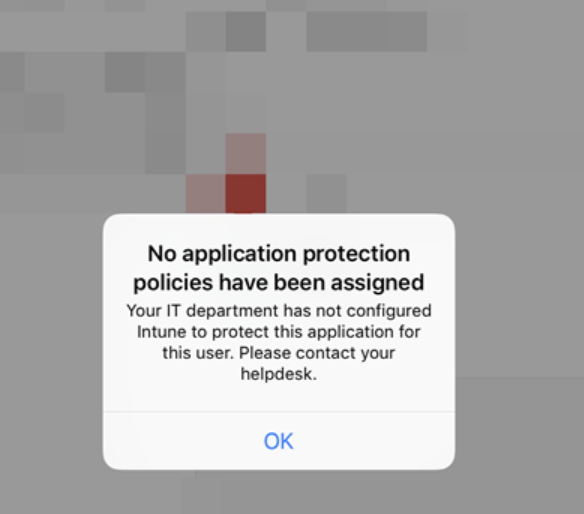
- When users try to setup Microsoft Outlook on their mobile devices, there is no application assigned. Solution: Ensure the user has assigned licensed and is in the group assigned with App Protection policy.
- User will be prompted with setting up an organization PIN to access the app.
Solution: Update the MAM policy to instantly apply upon enrolment.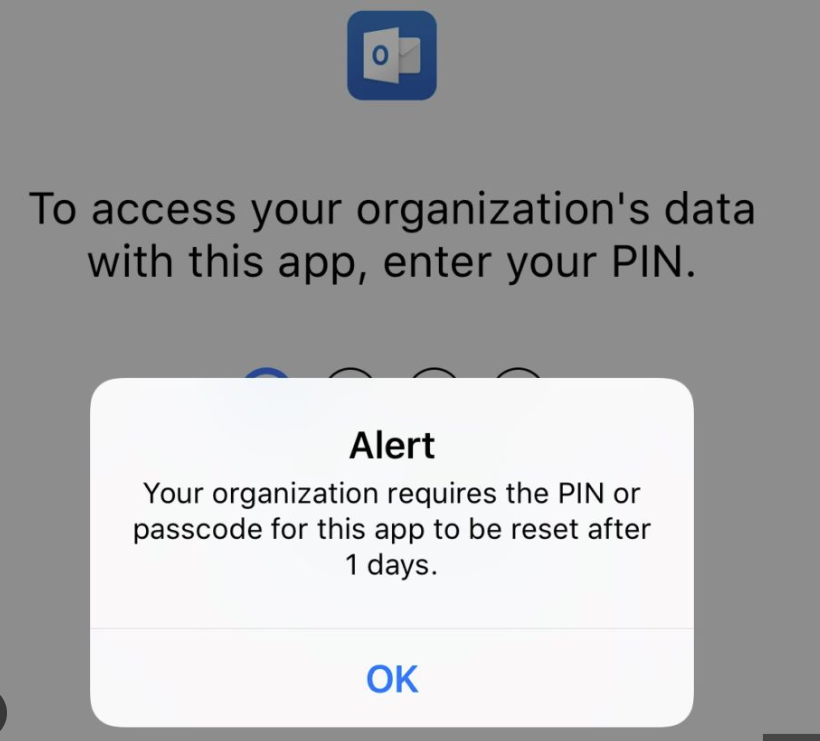
- Trying to setup the native iOS Mail app, which the iOS Mail App is not supported in MAM policy.
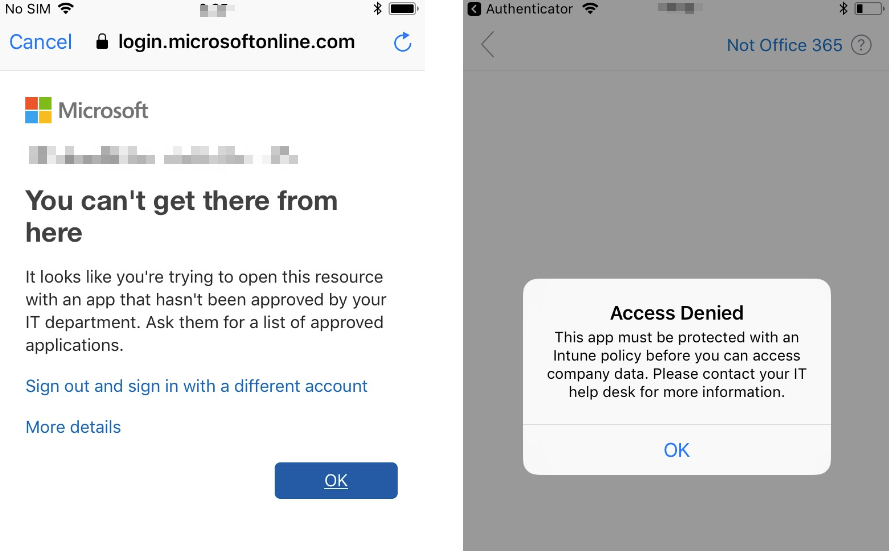
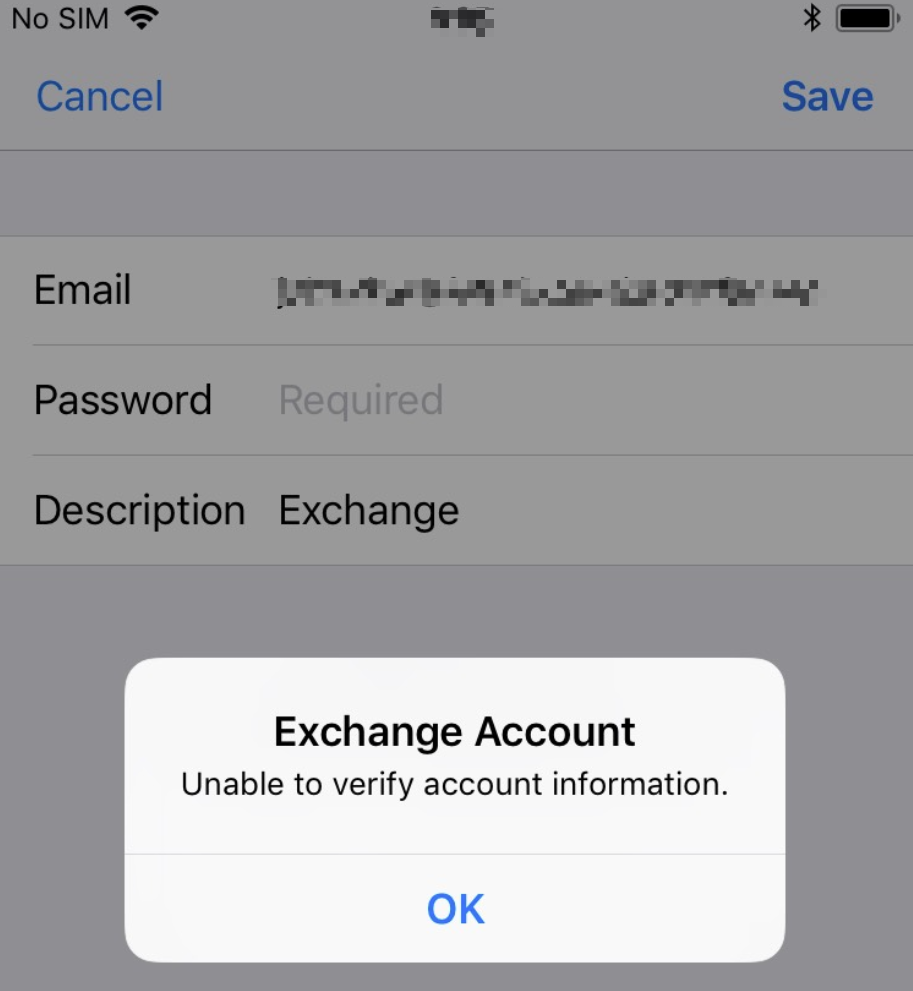
Solution: Download and install Outlook App from the App Store.
App Protection actions based on user status
This is a list of actions to take based on the user status:
- If the user isn't licensed for app protection, assign an Intune license to the user
- If the user isn't licensed for Microsoft 365, get a license for the user.
- If a user's app is listed as Not checked in, check if you've correctly configured an app protection policy for that app.
- Ensure that these conditions apply across all users to which you want app protection policies to apply.