How does MDM policy processing work on Windows devices with Microsoft Intune
Overview
This knowledge base article provides an overview of how the MDM policy processing work on Windows devices with Microsoft Intune.
Breakdown of traditional Group Policy (GPO)
With GPO it relies on Active Directory (AD) to store and distribute polices to domain-joined devices. These policies are stored in Group Policy Objects (GPO) linked to organizational units (OUs) within AD. When a policy is successfully deployed on a domain-joined device, the policies are deployed to HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft.
Breakdown of Microsoft Intune
When a device configuration in Microsoft Intune is created or modified and applied from that point forward to the endpoints (devices). This knowledge base article will explain will provide why policies are deployed to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\providers.
When device configuration profiles are created in Microsoft Intune, those settings can be assigned to users or devices. Once the assignment has taken place and the user or the device is a member of the group to which the policy is applied that user or device will receive the policy on the next policy check interval whereby the policy check interval is every 8 hours. Users are able to force a policy check either using Company Portal or Access Work or School settings (Settings > Accounts > Access work or school). The MDM (Mobile Device Management) protocol client will take care of applying the policies to the client.
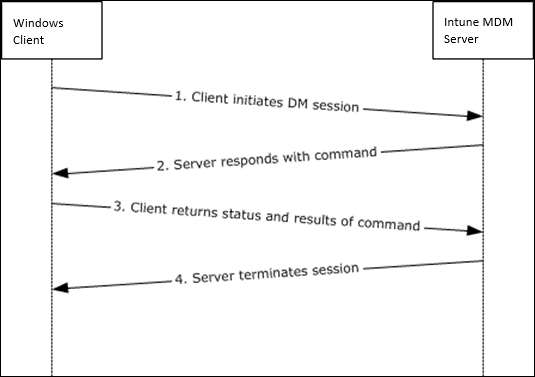
Mobile Device Management Protocol
Windows 10/11 has built in support for the Mobile Device Enrollment Protocol (MS-MDE), and devices rolled out using this protocol can be managed using the Mobile Device Management Protocol (MS-MDM). MS-MDM is a subset of the Open Mobile Association (OMA) Device Management Protocol (OMA-DM).
When Windows 10/11 is managed through MDM, it configures using Configuration Service Provider (CSP) Settings which expose device configuration settings. Possible settings are added (and removed) with each new Windows 10/Windows 11 version Microsoft release. By using Microsoft Intune, you are able to read, set, modify, or delete configuration settings on the device.
For a combination of protocols that allow communication between the device and MDM server:
Enrollment Protocol: This sets up the initial communication between the device and MDM server. It uses a process involving Discovery, Certificate installation, and DM Client provisioning using protocols like OMA DM XML over HTTPS [1].
Management Protocol: Once enrolled, the device uses protocols like SMS-MDM (SyncML over HTTPS) to communicate with the MDM server. This allows the server to send policies, apps, and security configurations to the device [2].
The role of Configuration Service Provider (CSPs):
Intune leverages Configuration Service Providers (CSPs) to translate its policies into settings on the target device. Each CSP caters to a specific configuration area, like Wi-Fi, BitLocker, or password policies. When an Intune policy is assigned, the corresponding CSP takes action, modifying relevant registry keys under HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\providers\<GUID>. Where <GUID> acts as a unique identifier for the particular CSP involved.
CSPs receive configuration policies in the XML-based Synchronization Markup Language (SyncML) format, pushed from an Microsoft Intune. CSPs can be configured either from the Microsoft Endpoint Manager portal using the GUI when made available by Microsoft. The CSP settings can be found here.
+-----------------------------------+
| HKEY_LOCAL_MACHINE |
+-----------------------------------+
| ... |
+-----------------------------------+
| SOFTWARE |
+-----------------------------------+
| ... |
+-----------------------------------+
| Microsoft |
+-----------------------------------+
| ... |
+-----------------------------------+
| PolicyManager |
+-----------------------------------+
| providers | (Stores Intune Policies via CSPs)
+-----------------------------------+
| | |
| +-- <GUID1> | (Example: BitLocker Encryption)
| | ... |
| | default | (Device or User Specific Policies)
| | ... |
| | Device | (Device Policies)
| | ... |
| | Policies | (Specific Policy Settings)
| | ... |
| +-- <GUID2> | (Example: Wi-Fi Configuration)
| ... |
| ... |
+-----------------------------------+
Examples: Policies Stored in HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\providers:
1. **BitLocker Drive Encryption:** Policies enforcing BitLocker encryption can be stored under this path with the `Microsoft-Windows-Security-Auditing` CSP. The registry key contain settings like minimum drive encryption strength or automatic encryption triggers.
2. **Wi-Fi Configuration:** Intune policies establishing Wi-Fi profiles might be stored under a CSP like `Microsoft-Windows-NetworkConnectivity`. The registry includes details like SSID, password, and security type for the Wi-Fi network.
3. **Password Complexity:** Policies enforcing minimum password length, complexity requirements, or password expiration can be stored with a CSP like `Microsoft-Windows-DeviceManagement-Enterprise MDM`. The registry hold values for minimum password length or character type requirements.
4. **Mobile Device Management (MDM) Restrictions:** Policies restricting device functionality like camera usage or data encryption can be stored under a relevant CSP. The registry contains like disabling the camera app or enforcing encryption for on-device data.
5. **Operating System Updates:** Intune policies for managing Windows Update settings or deferral periods might be stored under a CSP like `Microsoft-Windows-Update`. The registry includes values for deferral periods or automatic update configuration.
6. **Application Management:** Policies deploying applications or managing app permissions can be stored under an application-specific CSP. The registry contains like installation paths or permission settings for the managed application.
7. **Device Health Monitoring:** Intune policies for configuring health reporting or compliance checks might be stored under a CSP like `Microsoft-Windows-DeviceManagement-Enterprise MDM`. The registry hold settings for reporting frequency or specific compliance checks to be performed.
8. **Remote Lock and Wipe:** Policies allowing remote device lock or data wipe in case of loss or theft can be stored under a relevant CSP. The registry contains settings for enabling remote wipe functionality or triggering conditions.
9. **Security Baselines:** Intune policies enforcing specific security configurations (e.g., firewall settings) can be stored under a security-focused CSP. The registry hold values for firewall rules or other security-related configurations
The role of OMA-URI:
If settings cannot be set in the GUI of Microsoft Intune but are available as a CSP, this can be set using OMA-URI configuration. By creating a custom profile type when creating a configuration policy. It’s expected though that with the introduction of the Settings Catalog where all possible settings will be made available through the Settings Catalog.
In the end, either the setting created using a GUI option, or by specifying the OMA-URI configuration, the policy that the endpoint receive are based on the OMA-URI settings. Keep in mind that the behavior of a CSP depends on the CSP. Some CSPs remove the setting, and some CSPs keep the setting, also called tattooing.
The role of Settings Catalog:
Settings Catalog plays a key role in simplifying device configuration management within Microsoft Intune. It provides centralized repository which allows Settings Catalog acts as a one-stop shop for all configurable settings supported by Intune for various device platforms (Windows, iOS/iPadOS, macOS, etc.). It also aims to encompass all settings previously accessible through individual templates or custom profiles. With Setting Catalog, it simplifies discovery which allows your administrators to easily search for and identify the desired configuration options.