ACSC Essential Eight
The ACSC Essential Eight Maturity Model (E8) is a set of 8 security strategies for Windows devices, each containing several security controls. Controls are linked to 3 Maturity Levels (ML1, ML2, ML3) in increasing levels of assurance. For example, ML3 has all controls and shorter timeframes, like time between release of a Windows update and deployment to devices.
Customers can opt-in to E8 at a particular level and receive content cumulative to that level (eg E8 ML2 = ML1 + ML2). At the moment, this means several configuration policies. Note that some controls (like “user app hardening”) require the deployment of third-party security guidelines like the Microsoft Edge Security Baseline.
The ACSC also provide an Essential Eight Maturity Verification Tool (E8MVT) to ACSC Partners, which some customers will use to verify our configuration. It’s currently a set of PowerShell scripts with several bugs and caveats. Please contact support if you encounter any issues.
Profiles
We deploy the following Settings Catalog profiles:
-
ACSC E8 Nov 2023 - ML1 App control - Audit batch scripts
-
ACSC E8 Nov 2023 - ML1 App control - Block batch scripts
-
ACSC E8 Nov 2023 - ML1 App control - Audit
-
ACSC E8 Nov 2023 - ML1 App control - Block
-
ACSC E8 Nov 2023 - ML2 App control - Audit
-
ACSC E8 Nov 2023 - ML2 App control - Block
-
ACSC E8 Nov 2023 - ML3 App control - Audit
-
ACSC E8 Nov 2023 - ML3 App control - Block
-
ACSC E8 Nov 2023 - ML1 Restrict admin privileges
-
ACSC E8 Nov 2023 - ML3 Restrict admin privileges
-
ACSC E8 Nov 2023 - ML1 Restrict Office macros - Allow with prompt
-
ACSC E8 Nov 2023 - ML1 Restrict Office macros - Block
-
ACSC E8 Nov 2023 - ML2 Restrict Office macros
- ACSC E8 Nov 2023 - ML3 Restrict Office macros - Allow with trusted publishers
-
ACSC E8 Nov 2023 - ML1 User app hardening - MS Edge
-
ACSC E8 Nov 2023 - ML2 User app hardening
-
ACSC E8 Nov 2023 - ML2 User app hardening - ACSC Office Guidance
-
ACSC E8 Nov 2023 - ML2 User app hardening - Chrome Security Guide
-
ACSC E8 Nov 2023 - ML2 User app hardening - MS Edge Security Baseline
- ACSC E8 Nov 2023 - ML2 User app hardening - MS Office Security Baseline
-
ACSC E8 Nov 2023 - Trusted Publishers
And the following custom config profiles:
- ACSC E8 Nov 2023 - ML2 User app hardening - ACSC Office Guidance (custom)
Customers will also need
-
Devicie Foundation
- Windows LAPS
- Back catalog and Windows Update rings of 1 month or less
-
WDAC Managed Installer enabled for ML2 or ML3 app control
-
Account Protection group membership policy adding admins to the Guests group
- Devicie policies remove admin rights, but some auditors expect admin logon to be completely blocked as that's the typical implementation in Active Directory environments
-
Limit their usage of certain app types, since we don’t have hardening policies for others
-
Office productivity suite: only Office
-
Web browsers: Microsoft Edge or Google Chrome
-
PDF software: Microsoft Edge or Adobe Acrobat
-
Microsoft Office
Signed add-ins or macros can be allowed via Trusted Publisher at ML2 and above. Some add-ins ship with Office but most people don’t use them. This PowerShell script can generate an Intune custom config policy for a specific add-in file (usually shown in an error message):
<#
.SYNOPSIS
Retrieves trusted publisher certificates from files and converts them to Intune config.
.DESCRIPTION
This script retrieves signer certificates from signed files, known as Trusted Publishers, and converts them to an Intune DCv1 omaSettings payload for deployment.
It is useful for allowing add-ins or macros in environments that require an allowlist of Trusted Publishers, like Essential Eight ML2 or CIS Office.
Certificate metadata can be converted back from Intune config by copying the value into cyberchef.tplant.com.au and using its Parse x.509 operation in Base64 mode.
.EXAMPLE
Get trusted publishers from Office add-ins.
Get-TrustedPublisherFromFile -Name "OneNote notes for Outlook" -Path "$env:ProgramFiles\Microsoft Office\root\Office16\ONBttnOL.dll" | ConvertTo-Json | clip
.EXAMPLE
Get trusted publishers from the Teams add-in.
Get-TrustedPublisherFromFile -Name "Microsoft Teams Meeting Add-in" -Path "$env:LOCALAPPDATA\Microsoft\TeamsMeetingAdd*\*\*\Microsoft.Teams.AddinLoader.dll" | ConvertTo-Json | clip
#>
[CmdletBinding()]
param(
# Display name of the app to show in Intune.
[Parameter(Mandatory)]
[string]$Name,
# Path or pattern for files to get the trusted publishers from.
[Parameter(Mandatory, ValueFromPipeline)]
[System.IO.FileInfo]$Path
)
$Path | Get-AuthenticodeSignature | Select-Object -ExpandProperty SignerCertificate -Unique | Select-Object @{
n = "@odata.type";
e = { "#microsoft.graph.omaSettingString" }
}, @{
n = "displayName";
e = { $_.Thumbprint }
}, @{
n = "description";
e = { $Name }
},
@{
n = "omaUri";
e = { "./Device/Vendor/MSFT/RootCATrustedCertificates/TrustedPublisher/$($_.Thumbprint)/EncodedCertificate" }
}, @{
n = "value";
e = { [System.Convert]::ToBase64String($_.RawData) }
}
To skip booting a VM and installing, you can dump MSIs to disk: msiexec /a "$pwd\Downloads\ZoomOutlookPluginSetup (1).msi" TARGETDIR="$pwd\Downloads\ZoomOutlook"
Our Trusted Publishers baseline uses the following script to update the certs for certain supported apps:
Get-ChildItem "$env:LOCALAPPDATA\Microsoft\TeamsMeetingAdd*" -Recurse -Include Microsoft.Teams.AddinLoader.dll | Get-TrustedPublisherFromFile.ps1 -Name "Microsoft Teams Meeting Add-in"
Get-ChildItem "$env:ProgramFiles\Adobe\Acrobat DC\PDFMaker\Mail\Outlook" -Recurse -Include SendAsLinkAddin.dll | Get-TrustedPublisherFromFile.ps1 -Name "Adobe Acrobat PDFMaker"
Get-ChildItem "${env:ProgramFiles(x86)}\Zoom\Zoom Outlook Plugin" -Recurse -Include ZoomOutlookPlugin*.dll | Get-TrustedPublisherFromFile.ps1 -Name "Zoom Outlook Plugin"
To check the expiry dates:
Get-ChildItem ... | Get-AuthenticodeSignature | Select-Object -ExpandProperty SignerCertificate | Select-Object NotAfter
|
Name |
Expiry |
|---|---|
|
Microsoft Teams Meeting Add-in |
07/5/2026 |
|
Adobe Acrobat PDFMaker |
05/11/2025 |
|
Zoom Outlook Plugin |
14/1/2026 |
Allowing Macros
Why do certain Office files or add-ins stop working?
The Essential Eight prohibits execution of Office macros without a business requirement. These can often be identified by specific file extensions eg .xlam for Excel. In add-ins that load macro files like Modano, a blocked macro can be identified by the HRESULT error code 0x800A03EC.
At ML1 or ML2, any macro can be allowed if the business requirement is identified for specific users. Technically it should be on a per-application basis but some customers may find this too complex to manage.
At ML3, only macros signed by certificates in the Trusted Publishers store can be allowed. Some applications like Modano may add their signing certificate to the store, but certificates can also be added via Intune. We have a base policy called Trusted Publishers to help with this. You can check whether a macro is signed by extracting it like a zip file, and opening the root (eg xl for Excel). If the macro is signed, there will be files matching the pattern vbaProjectSignature*.bin. The signing certificate can be extracted using the following script. It’s recommended to document the expiry date of the certificate.
<#
.SYNOPSIS
Gets the leaf signing certificate of a VBA project file.
.DESCRIPTION
This script extracts the signature from a signed VBA project file, carves out the last signing certificate (the leaf), and parses it into an X509Certificate2 object.
.EXAMPLE
.\Get-OfficeVBASigner.ps1 -Path macro.xlam
.EXAMPLE
.\Get-OfficeVBASigner.ps1 -Path macro.xlam -SignatureFile vbaProjectSignature.bin
#>
param (
[Parameter(Mandatory)]
[System.IO.FileInfo]$Path # Path to a signed VBA project file
)
# Open the VBA project as a zip archive
Add-Type -AssemblyName System.IO.Compression.FileSystem
$zipArchive = [System.IO.Compression.ZipFile]::OpenRead($Path)
# Find the signature file, prioritising by type in this order: V3, Agile, Legacy
$entry = $zipArchive.Entries | Where-Object Name -like "vbaProject*.bin" | Sort-Object -Descending | Select-Object -First 1
if (-not $entry) {
throw "No signature found"
}
# Read the signature
$memoryStream = New-Object System.IO.MemoryStream
$entry.Open().CopyTo($memoryStream)
$signature = $memoryStream.ToArray()
$zipArchive.Dispose()
# Magic bytes. DER is 0x30 0x82, but more bytes are available in real files and necessary for accuracy
$magicBytes = [byte[]](0x30, 0x82, 0x06, 0x64, 0x30, 0x82)
# Leaf signer is the last certificate, and the store is close to the end, so we search from the end of the file
# https://learn.microsoft.com/en-us/openspecs/office_file_formats/ms-oshared/715a782b-aacd-4743-acad-ab3c55d694ee
$startCertIndex = -1
for ($i = $signature.Length - $magicBytes.Length - 1; $i -ge 0; $i--) {
if ([Collections.Generic.SortedSet[String]]::CreateSetComparer().Equals($signature[$i..($i + $magicBytes.Length - 1)], $magicBytes)) {
$startCertIndex = $i
break
}
}
if ($startCertIndex -eq -1) {
throw "Certificate magic bytes not found"
}
# Carve out DER certificate
$certLength = [BitConverter]::ToInt32($signature, $startCertIndex - 4)
$cert = [byte[]]$signature[$startCertIndex..($startCertIndex + $certLength - 1)]
[System.Security.Cryptography.X509Certificates.X509Certificate2]::new($cert)
Once the Office app and users are identified, has a script to generate an overlay for specific required apps. Or you can just allow trusted publishers for all apps. User groups should be excluded from the “Block Office macros” policy and targeted with the allow policy.
Allowing Outlook add-ins
The Essential Eight macro hardening guide requires “Apply macro security settings to macros, add-ins and additional actions" for Outlook, which disables add-ins by default (unlike the other Office apps). It forces customers to allow macros for anyone using desktop Outlook with the Microsoft Teams add-in, which can be almost all users in certain organisations. In our opinion, this goes against the spirit of the E8 and results in a less secure environment, so we're planning to remove this setting in Q2 2025 for all new deployments.
If add-ins are required like the Teams integration in the following screenshot, deploy an “Allow for trusted publishers” as above. The Trusted Publishers baseline policy trusts the Teams add-in.
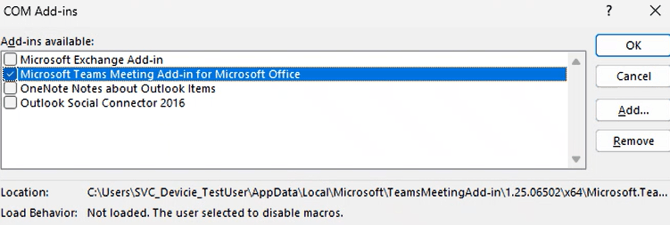
Essential Eight ML2 requires vendor hardening, which includes the Microsoft Office Security Baseline and the ACSC Office Hardening Guide. Both frameworks currently block opening or saving older Office file formats. These can usually be identified by the extension eg xls
Why are there multiple Office policies for the same control?
Microsoft 365 Business Premium does not support Group Policy, so we provide additional registry-based policies. These policies do not conflict and should be assigned to the same group. Enterprise Office versions and the Project or Visio apps will automatically use the stricter policies. The following settings aren't available with the registry-based policies:
- Block macro execution from the internet. This is enabled by default and can't be disabled on Business SKUs
- Automation security level. Implemented by other settings
- Disable VBA for Office applications. Implemented by other settings
- Macro runtime scan scope
- Allow mix of policy and user locations. Not relevant for user-registry-based policies
- Outlook apply macro security settings to add-ins. Very high user impact, minimal security value
Google Chrome
When downloading files, some file types are blocked. Which types are blocked or allowed?
The E8 “user app hardening” strategy requires implementation of vendor hardening guidance. This is currently the 2021 Chrome Browser Enterprise Security Configuration Guide. It includes the DownloadRestrictions policy which blocks the following files:
-
files flagged by Safe Browsing as DANGEROUS_ACCOUNT_COMPROMISE or DANGEROUS
-
download URLs flagged by Safe Browsing
-
files that have a danger_level of DANGEROUS and ALLOW_ON_USER_GESTURE.
All other files are allowed. danger_level is the most common cause of blocked files. The list of file types and their danger_level is maintained by the Chromium team and available here: download_file_types.asciipb - Chromium Code Search. In the past, it has included any executable files eg MSI/exe, but this is often fine because the E8 “application control” strategy requires blocking these files in most scenarios.
If a customer needs to bypass the policy, they can copy the file download URL and use this PowerShell snippet: Invoke-WebRequest <download url> -OutFile <filename>
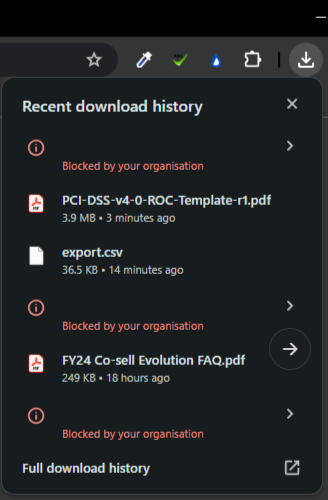
Not at the moment. An overlay policy can be used to lower DownloadRestrictions to one of the following options, but customers would need to risk accept the deviation from E8 ML2.
-
Block malicious downloads. Blocks files flagged as DANGEROUS, DANGEROUS_HOST, ACCOUNT_COMPROMISE, or if the URL is flagged by Safe Browsing
-
No special restrictions. Currently the default

Remote Desktop
Why do I receive the following error when using the Remote Desktop app?
This error commonly occurs with Windows 365, Azure Dev Box, or Azure Virtual Desktop.
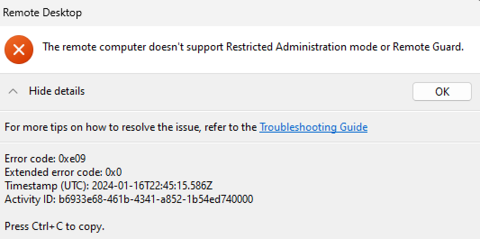
The E8 “restrict admin privileges” strategy requires implementation of Remote Credential Guard at ML3. It has several limitations:
-
Can only connect to a device that is joined to an Active Directory domain
-
Can only connect directly, not via Remote Desktop Connection Broker and Remote Desktop Gateway
-
Requires Kerberos authentication
If the customer does not have an Active Directory domain, cannot join their remote device to Active Directory, or is using RDCB/RDG, ask the customer for a group containing users that need access. Then create an overlay that disables device_vendor_msft_policy_config_admx_credssp_restrictedremoteadministration (tags: enabled: false), assign to the group, and exclude the group from the “Restrict admin privileges” overlay.
If the customer meets the requirements, follow standard Kerberos troubleshooting
-
Run klist command on the connecting device to check for tickets
-
If using Windows Hello for Business, ensure cloud Kerberos or equivalent is configured
-
etc
PowerShell
Transcript Logging
Maturity Level 3 requires PowerShell Transcript Logging. It logs to Documents by default (OneDrive, local, or SYSTEM’s systemprofile\Documents). There are reports that some PowerShell versions log to $pwd by default when executing as SYSTEM, but I haven't been able to replicate.
These locations can cause user confusion and may not be desired if scripts contain sensitive information. Instead, we configure all transcripts to use C:\Windows\system32\config\systemprofile\Documents.
Attack Surface Reduction (ASR) rules
How can I add exclusions to the Devicie ASR rules?
Contact support to disable the ASR setting in your overlays - currently CIS, ACSC Office Hardening Guidance, E8 user app hardening, and E8 macro allow/block. Then you can create your own policy and self-manage the rules and exemptions. Relevant Microsoft doc. If you have Defender for Endpoint, a report is available to track ASR audit and block events.
Why does the E8MVT or other tools show failures for ASR rules?
Our Intune policies use the Defender CSP to configure ASR rules, instead of the Policy CSP. This is the same CSP used by the Endpoint Security blade for enrolled devices. It supports more features, like not conflicting if multiple policies enable the same rule, and it supports exclusions too. However, some security tools may only check for the old GPO regkeys (same as Policy CSP).
The E8MVT has been updated to support the Defender CSP, but must be executed as admin as the Defender PolicyManager regkey is only readable by admins. Customers can also execute the following PowerShell snippet to list ASR rules on a device by GUID.
Get-MpPreference | select -exp AttackSurfaceReductionRules_Ids
Get-MpPreference | select -exp AttackSurfaceReductionRules_Actions
The actions correspond to the state of a rule, eg 1 indicates the corresponding rule is in block mode. Customers can use the Microsoft reference to convert the GUID to a rule name.
Why does the E8MVT show a failure for batch files?
Some kind of exception occurred: This command cannot be run due to the error: Access is denied.
Airlock blocks batch files (%temp%\BATTest.bat) in a way that the tool does not detect.
Why does the E8MVT show failures for the Microsoft recommended block rules?
Some kind of exception occurred: Access to the path is denied.
The tool uses Add-Type to assess recommended rules, which is blocked by Airlock (see above). However, the tool only checks for WDAC block rules, not Airlock, so it would fail anyway. Customers should review Airlock configuration manually to ensure the following files and drivers are blocked:
-
Applications that can bypass WDAC and how to block them - Windows Security | Microsoft Learn
-
Microsoft recommended driver block rules - Windows Security | Microsoft Learn
Application Control
Devicie uses Windows Defender Application Control at all maturity levels, to simplify allowlisting with the Managed Installer feature. Follow these instructions to enable the feature, since Microsoft's API doesn't allow us to enable it automatically. Once enabled, future app installations from Intune (like the Devicie app catalog) will be allowed automatically. Note that existing apps will remain blocked, so we don't recommend deploying application control for existing devices.
Manual allowlisting by creating supplemental policies is necessary in the following cases:
- Self-updating apps, particularly user-context apps. The Devicie app report can help to find these
- Packaged apps (AppX or MSIX) that aren't from the Microsoft Store
- Apps that were installed manually
To avoid needing multiple supplemental policies, you can choose to only use one base policy (eg ML1 or ML2 but not both).
Credential Guard
Why does the E8MVT show failures for Credential Guard?
Remote Credential guard is disabled
Credential guard is disabled
Credential guard is not running
Credential Guard currently requires Windows Enterprise or Education.
LSA Protection
Why does the E8MVT show failures for LSA protection?
Configuration via Intune policies requires at least Windows 11 22H2.
Patching
Browsers
Why does the E8MVT show failures for browser patching at ML3?
The tool currently requires browsers to be patched within 48 hours, even though the corresponding E8 control only requires this timeframe if a critical or exploited vulnerability is present.